Several years back I had my first stint at building a strategic security road map to a client I was working with. I must say I was not a practiced and seasoned expert who knew “a-z” of building security strategies and road maps. So as usual, I just rolled up my sleeves and started digging in to finding out all I can about what needs to be done, who are involved , what should be my approach and thousand other questions I had. This did lead me down many rabbit holes, and after several years of researching, discussing with experts, working with security architects and many implementations later, I have come a little bit further down the road of implementing security strategies and I assume I am bit wiser (so I would like to think).
In this blog series I will try to impart what I have learnt so far in my journey in helping multiple clients implement security road maps from undersetting the need, planning, documenting, getting the buy in, to implementing security road maps.
So the first thing I needed to understand was the big “WHY”
Why do we need implement a security strategy in the first place? my take on it and as I see it, was for any organization to ensure that their “valuables”, such as information technology or systems or data are kept safe from unwanted access and usage.
Well, what does that mean then ?
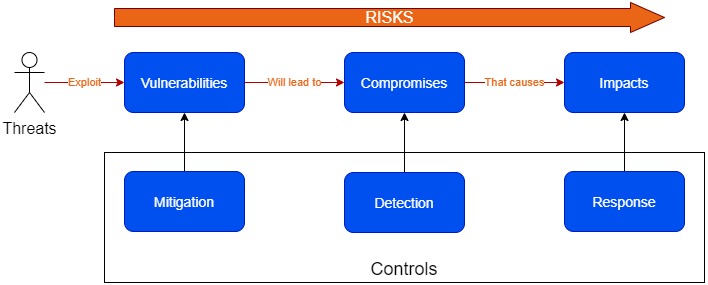
Well, any organization has things that they value , such as data, systems, devices, or any other components that has business value to the organization, which are called “Assets“. Through a weakness in the organizations environment called “Vulnerabilities“, assets can be exploited by intruders called “Threats“. Hence these are the “Risks” that any organization will face. When building our strategy we are suppose to identify these risks and come up with plans, designs, and actions to mitigate these risks. We have to do this by putting relevant controls in place
When defining risks and their corresponding controls, we will need to consider
- The opportunity for threats to exploit vulnerabilities with controls for mitigation.
- The chance that a vulnerability will lead to a compromise by using controls for detection.
- The effect that a compromise has, in terms of impact by using controls to response.
In order to implement a strategy we will need to come up with a strategy that allows an organization continuously look at,
- Planning – studying and then designing a resistant security architecture for various IT projects in line with business needs and risk acceptance
- Developing – prerequisites for networks, firewalls, routers, and other network devices
- Performing – vulnerability assessment, security testing, and risk analysis
- Researching – the updated security standards, systems, regulatory frameworks and best practices
- Communicating – relevant risks, vulnerabilities, and mitigation strategies to senior leadership
So how do we go about doing this…
Well, this is just the start on my approach to enable an organization to implement a security road map. In my next articles I dive a bit deeper, by taking a case study on an actual implementation of a strategic security roadmap, what was learnt, what went right , what failed, and some tips and tricks .